- In order to achieve this, Buildroot is able to generate a cross-compilation toolchain, a root. Scp for downloads of tarballs over SSH with scp.
- Previous message: Buildroot PATCH package/autossh: do not look for the host's ssh command.
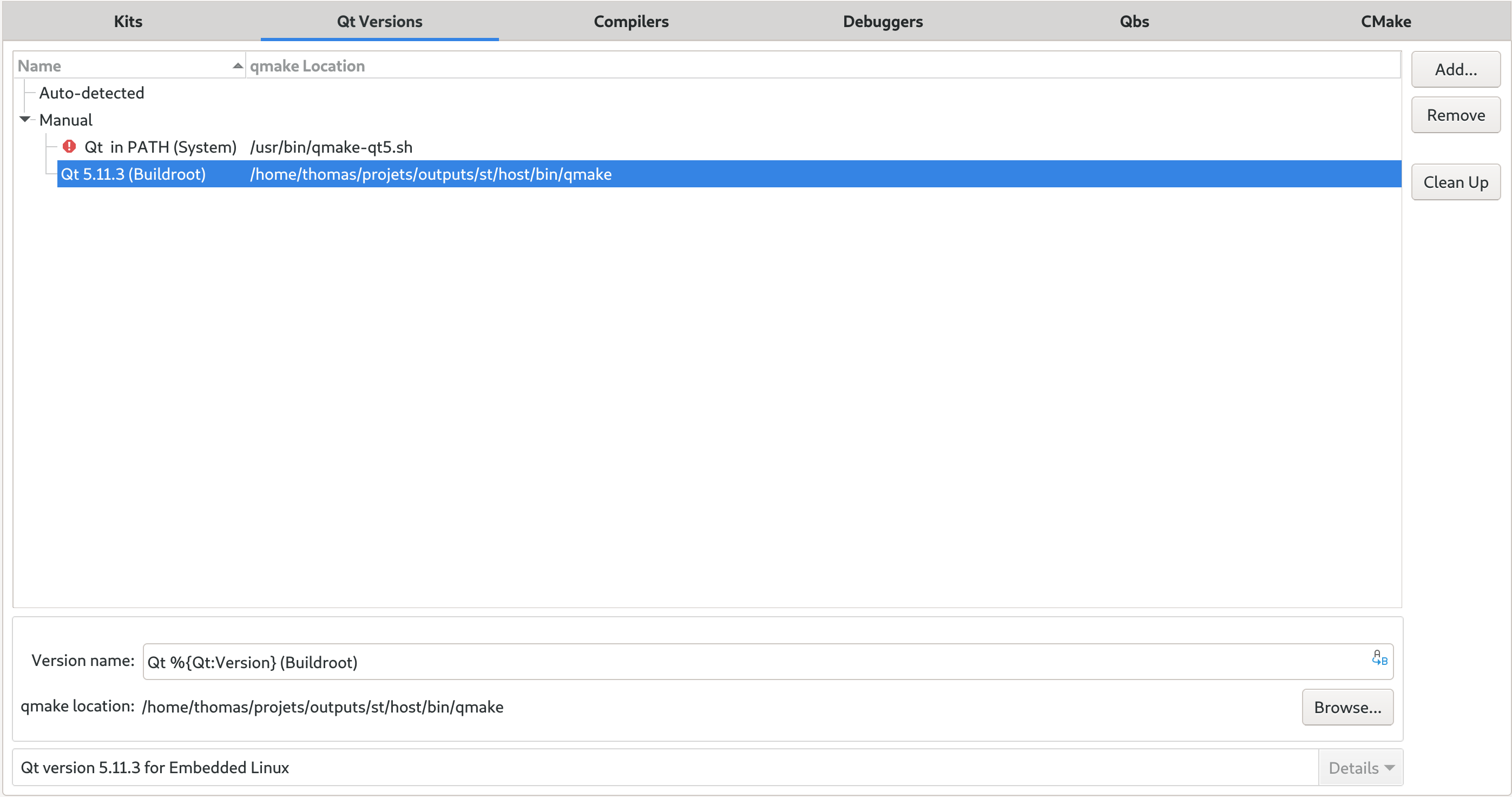
Buildroot is a tool that simplifies and automates the process ofbuilding a complete Linux system for an embedded system, usingcross-compilation. In order to achieve this, Buildroot is able to generate across-compilation toolchain, a root filesystem, a Linux kernel imageand a bootloader for your target.
Buildroot Ssh Connection Refused
Buildroot Sshd_config
Buildroot Ssh-keygen
| Commit message (Collapse) | Author | Age | Files | Lines | |
|---|---|---|---|---|---|
| * | package/openssh: security bump to version 8.5p1 | Fabrice Fontaine | 2021-03-28 | 2 | -7/+9 |
| |||||||||||||||||||||||||||||||||| | * ssh-agent(1): fixed a double-free memory corruption that was introduced in OpenSSH 8.2 . We treat all such memory faults as potentially exploitable. This bug could be reached by an attacker with access to the agent socket. On modern operating systems where the OS can provide information about the user identity connected to a socket, OpenSSH ssh-agent and sshd limit agent socket access only to the originating user and root. Additional mitigation may be afforded by the system's malloc(3)/free(3) implementation, if it detects double-free conditions. The most likely scenario for exploitation is a user forwarding an agent either to an account shared with a malicious user or to a host with an attacker holding root access. * Portable sshd(8): Prevent excessively long username going to PAM. This is a mitigation for a buffer overflow in Solaris' PAM username handling (CVE-2020-14871), and is only enabled for Sun-derived PAM implementations. This is not a problem in sshd itself, it only prevents sshd from being used as a vector to attack Solaris' PAM. It does not prevent the bug in PAM from being exploited via some other PAM application. GHPR#212Also license has been updated to add some openbsd-compat licenses:https://github.com/openssh/openssh-portable/commit/922cfac5ed5ead9f796f7d39f012dd653dc5c173https://www.openssh.com/txt/release-8.5Signed-off-by: Fabrice Fontaine <fontaine.fabrice@gmail.com>Signed-off-by: Yann E. MORIN <yann.morin.1998@free.fr> | ||||
| * | package/openssh: security bump to version 8.4p1 | Christian Stewart | 2021-03-01 | 2 | -4/+4 |
| ||||||||||||| | Fixes CVE-2020-15778: scp in OpenSSH through 8.3p1 allows command injection inthe scp.c toremote function, as demonstrated by backtick characters in thedestination argument. NOTE: the vendor reportedly has stated that theyintentionally omit validation of 'anomalous argument transfers' because thatcould 'stand a great chance of breaking existing workflows.'https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2020-15778Signed-off-by: Christian Stewart <christian@paral.in>Signed-off-by: Peter Korsgaard <peter@korsgaard.com> | ||||
| * | Replace LIBFOO_CPE_ID_VERSION_MINOR by LIBFOO_CPE_ID_UPDATE | Fabrice Fontaine | 2021-01-31 | 1 | -1/+1 |
| |||||||||| | Replace LIBFOO_CPE_ID_VERSION_MINOR by LIBFOO_CPE_ID_UPDATE to better'comply' with the official 'Well-Formed CPE Name Data Model' parameters: - https://csrc.nist.gov/publications/detail/nistir/7695/final - https://nvlpubs.nist.gov/nistpubs/Legacy/IR/nistir7695.pdfSigned-off-by: Fabrice Fontaine <fontaine.fabrice@gmail.com>Signed-off-by: Thomas Petazzoni <thomas.petazzoni@bootlin.com> | ||||
| * | package: provide CPE ID details for numerous packages | Matt Weber | 2021-01-04 | 1 | -0/+3 |
| |||||||| | This patch adds CPE ID information for a significant number ofpackages.Signed-off-by: Matthew Weber <matthew.weber@rockwellcollins.com>Signed-off-by: Thomas Petazzoni <thomas.petazzoni@bootlin.com> | ||||
| * | package/openssh: add optional dependency on audit | Norbert Lange | 2020-06-06 | 1 | -0/+7 |
| ||||| | Signed-off-by: Norbert Lange <nolange79@gmail.com>Signed-off-by: Thomas Petazzoni <thomas.petazzoni@bootlin.com> | ||||
| * | package/openssh: bump to version 8.3p1 | Baruch Siach | 2020-06-05 | 2 | -4/+4 |
| ||||||| | Format hash file with two spaces separators.Signed-off-by: Baruch Siach <baruch@tkos.co.il>Signed-off-by: Yann E. MORIN <yann.morin.1998@free.fr> | ||||
| * | package/openssh: allow separate selection of client, server, keyutils | Thomas De Schampheleire | 2020-05-09 | 2 | -4/+55 |
| ||||||||||||||||||||||||||||||||| | The openssh package comprises three separate entities: the SSH client, SSHserver, and some SSH key utilities. One may want the client but not theserver, the server but not the client, or maybe only the key utilities.Add separate options for each entity and update the files installed ontarget accordingly.On an ARM Cortex-A53 configuration, size of stripped binaries are:Client programs: 2213118 bytes (2161 KB)usr/bin/ssh,657180usr/bin/scp,99836usr/bin/ssh-add,312800usr/bin/ssh-agent,296428usr/libexec/ssh-keysign,398908usr/libexec/ssh-pkcs11-helper,292316usr/bin/sftp,144992usr/bin/ssh-copy-id,10658Server programs: 806840 bytes (787 KB)usr/libexec/sftp-server,112140usr/sbin/sshd,694168etc/init.d/S50sshd,532Key utilities: 789648 bytes (771 KB)usr/bin/ssh-keygen,398924usr/bin/ssh-keyscan,390724Signed-off-by: Thomas De Schampheleire <thomas.de_schampheleire@nokia.com>Signed-off-by: Thomas Petazzoni <thomas.petazzoni@bootlin.com> | ||||
| * | package/openssh: bump to version 8.2p1 | Romain Naour | 2020-04-04 | 2 | -3/+3 |
| ||||||||||||||||||| | This new version is mandatory to allow the glibc package bump to version 2.31.Otherwise it's not possible to connect to the remote host, as reported by [1] [2].Upstream commit [3][4] fixes the issue.[1] https://bugs.archlinux.org/task/65386[2] https://bugs.gentoo.org/708224[3] https://github.com/openssh/openssh-portable/commit/beee0ef61866cb567b9abc23bd850f922e59e3f0[4] https://github.com/openssh/openssh-portable/commit/69298ebfc2c066acee5d187eac8ce9f38c796630Release Note:https://www.openssh.com/txt/release-8.2Signed-off-by: Romain Naour <romain.naour@smile.fr>Reviewed-by: David Pierret <david.pierret@smile.fr>Tested-by: David Pierret <david.pierret@smile.fr>Signed-off-by: Thomas Petazzoni <thomas.petazzoni@bootlin.com> | ||||
| * | package: rely on systemctl preset-all for buildroot-provided services | Jérémy Rosen | 2019-12-18 | 1 | -3/+0 |
| |||||||||||| | All the packages in this list have the following properties* units are provided by buildroot in the package directory* the SYSTEMD_INSTALL_INIT_HOOK is exactly equivalent to what the [Install] section of the unit doesThe fix removes the soflinking in the .mk fileSigned-off-by: Jérémy Rosen <jeremy.rosen@smile.fr>Signed-off-by: Yann E. MORIN <yann.morin.1998@free.fr> | ||||
| * | package/openssh: bump to version 8.1p1 | Baruch Siach | 2019-10-15 | 2 | -4/+4 |
| ||||||||||| | This bump is not marked as security bump. The 8.1 release fixes a XMSSkey parsing code vulnerability. This code can not be enabled withoutexplicit definition of the WITH_XMSS macro.Update LICENCE hash; converted to UTF-8.Signed-off-by: Baruch Siach <baruch@tkos.co.il>Signed-off-by: Peter Korsgaard <peter@korsgaard.com> | ||||
| * | package/openssh: bump to version 8.0p1 | Adam Duskett | 2019-06-21 | 5 | -503/+3 |
| ||||||| | Also remove upstream patches.Signed-off-by: Adam Duskett <Aduskett@gmail.com>Signed-off-by: Thomas Petazzoni <thomas.petazzoni@bootlin.com> | ||||
| * | package/openssh: fix build with atomic | Fabrice Fontaine | 2019-04-26 | 1 | -2/+5 |
| |||||||||| | Use pkg-config to retrieve openssl dependencies such as atomicFixes: - http://autobuild.buildroot.org/results/33d0e56368ab0e74d523be4837824654a4684746Signed-off-by: Fabrice Fontaine <fontaine.fabrice@gmail.com>Signed-off-by: Peter Korsgaard <peter@korsgaard.com> | ||||
| * | openssh: add upstream security fixes | Baruch Siach | 2019-02-12 | 2 | -0/+461 |
| |||||||||||||||||||| | CVE-2019-6109: Due to missing character encoding in the progressdisplay, a malicious server (or Man-in-The-Middle attacker) can employcrafted object names to manipulate the client output, e.g., by usingANSI control codes to hide additional files being transferred. Thisaffects refresh_progress_meter() in progressmeter.c.CVE-2019-6111: Due to the scp implementation being derived from 1983rcp, the server chooses which files/directories are sent to the client.However, the scp client only performs cursory validation of the objectname returned (only directory traversal attacks are prevented). Amalicious scp server (or Man-in-The-Middle attacker) can overwritearbitrary files in the scp client target directory. If recursiveoperation (-r) is performed, the server can manipulate subdirectories aswell (for example, to overwrite the .ssh/authorized_keys file).Signed-off-by: Baruch Siach <baruch@tkos.co.il>Signed-off-by: Peter Korsgaard <peter@korsgaard.com> | ||||
| * | package/openssh: Add sysusers.d snippet | Chris Lesiak | 2019-02-06 | 2 | -4/+13 |
| ||||||||| | Whether using the new sysusers.d snippet, or adding an entry to/etc/password, set the service's home directory to /var/empty.See README.privsep included as part of the openssh distribution.Signed-off-by: Chris Lesiak <chris.lesiak@licor.com>Signed-off-by: Arnout Vandecappelle (Essensium/Mind) <arnout@mind.be> | ||||
| * | package/openssh: Set /var/empty permissions | Chris Lesiak | 2019-02-03 | 1 | -0/+4 |
| |||||||||||| | The openssh privilege separation feature, enabled by default,requires that the path /var/empty exists and has certain permissions(not writable by the sshd user). Note that nothing ever gets writtingin this directory, so it works fine on a readonly rootfs.See README.privsep included as part of the openssh distribution.Signed-off-by: Chris Lesiak <chris.lesiak@licor.com>Signed-off-by: Arnout Vandecappelle (Essensium/Mind) <arnout@mind.be> | ||||
| * | package/openssh: add upstream security fix | Baruch Siach | 2019-01-15 | 1 | -0/+39 |
| |||||||||||||| | Fixes CVE-2018-20685: The scp client allows server to modify permissionsof the target directory by using empty ('D0777 0 n') or dot ('D0777 0.n') directory name.The bug reporter lists a number of related vulnerabilities that are notfixed yet: https://sintonen.fi/advisories/scp-client-multiple-vulnerabilities.txtSigned-off-by: Baruch Siach <baruch@tkos.co.il>Signed-off-by: Peter Korsgaard <peter@korsgaard.com> | ||||
| * | package/openssh: use BR2_SYSTEM_DEFAULT_PATH as default PATH | Markus Mayer | 2018-12-31 | 1 | -0/+1 |
| |||||||||||| | We use the configuration option $(BR2_SYSTEM_DEFAULT_PATH) to set thedefault PATH in OpenSSH sessions.$(BR2_SYSTEM_DEFAULT_PATH) is a Kconfig string. So it is alreadyquoted, which is exactly what we want.Signed-off-by: Markus Mayer <mmayer@broadcom.com>Reviewed-by: 'Yann E. MORIN' <yann.morin.1998@free.fr>Signed-off-by: Thomas Petazzoni <thomas.petazzoni@bootlin.com> | ||||
| * | openssh: bump to version 7.9p1 | Baruch Siach | 2018-10-21 | 4 | -96/+3 |
| |||||||||| | Drop patch #1. uClibc no longer includes pthreads.h indirectly.Drop patch #2. The sys/param.h header is included indirectly through thelocal includes.h header since version 6.8p1.Signed-off-by: Baruch Siach <baruch@tkos.co.il>Signed-off-by: Peter Korsgaard <peter@korsgaard.com> | ||||
| * | openssh: security bump to version 7.8 | Baruch Siach | 2018-08-24 | 2 | -3/+3 |
| ||||||||||||| | Fixes CVE-2018-15473: user enumeration vulnerability due to not delayingbailout for an invalid authenticating user until after the packetcontaining the request has been fully parsed.Some OpenSSH developers don't consider this a security issue: https://lists.mindrot.org/pipermail/openssh-unix-dev/2018-August/037138.htmlSigned-off-by: Baruch Siach <baruch@tkos.co.il>Signed-off-by: Thomas Petazzoni <thomas.petazzoni@bootlin.com> | ||||
| * | openssh: bump to version 7.7p1 | Baruch Siach | 2018-04-10 | 7 | -149/+3 |
| ||||||| | Drop upstream patches, renumber the rest.Signed-off-by: Baruch Siach <baruch@tkos.co.il>Signed-off-by: Thomas Petazzoni <thomas.petazzoni@bootlin.com> | ||||
| * | package/openssh: also install ssh-copy-id script | Julien BOIBESSOT | 2018-02-08 | 1 | -0/+6 |
| ||||||||||||| | This script is useful to copy SSH keys between client and server [1] andinstalled on most distributions (for example on debian: [2]).[1] https://www.ssh.com/ssh/copy-id[2] https://packages.debian.org/fr/jessie/armhf/openssh-client/filelistSigned-off-by: Julien BOIBESSOT <julien.boibessot@armadeus.com>Reviewed-by: 'Yann E. MORIN' <yann.morin.1998@free.fr>[Thomas: use full destination path.]Signed-off-by: Thomas Petazzoni <thomas.petazzoni@bootlin.com> | ||||
| * | package/*/Config.in: fix help text check-package warnings | Thomas Petazzoni | 2017-12-18 | 1 | -2/+3 |
| ||||||||||||| | This commit fixes the warnings reported by check-package on the helptext of all package Config.in files, related to the formatting of thehelp text: should start with a tab, then 2 spaces, then at most 62characters.The vast majority of warnings fixed were caused by too long lines. Afew warnings were related to spaces being used instead of a tab toindent the help text.Signed-off-by: Thomas Petazzoni <thomas.petazzoni@free-electrons.com> | ||||
| * | openssh: fix getpagesize() related static linking issue | Peter Korsgaard | 2017-11-01 | 1 | -0/+35 |
| |||||||||||||||||| | Fixes:http://autobuild.buildroot.net/results/8cc/8cc30818a400c7a392a3de787cabc9cd8425495f/The configure script checks for getpagesize() and sets HAVE_GETPAGESIZE inconfig.h, but bsd-getpagesize.c forgot to include includes.h (whichindirectly includes config.h) so the checks always fails, causing linkerissues when linking statically on systems with getpagesize().Fix it by including includes.h.Patch submitted upstream:https://lists.mindrot.org/pipermail/openssh-unix-dev/2017-October/036413.htmlSigned-off-by: Peter Korsgaard <peter@korsgaard.com>Signed-off-by: Thomas Petazzoni <thomas.petazzoni@free-electrons.com> | ||||
| * | openssh: security bump to version 7.6p1 | Peter Korsgaard | 2017-10-27 | 2 | -3/+5 |
| ||||||||||||| | Fixes CVE-2017-15906 - The process_open function in sftp-server.c in OpenSSHbefore 7.6 does not properly prevent write operations in readonly mode,which allows attackers to create zero-length files.For more details, see the release notes:https://www.openssh.com/txt/release-7.6Also add a hash for the license file while we're at it.Signed-off-by: Peter Korsgaard <peter@korsgaard.com> | ||||
| * | openssh: don't download patch from Github | Thomas Petazzoni | 2017-07-03 | 6 | -6/+109 |
| |||||||| | Patches downloaded from Github are not stable, so bring them in thetree.Signed-off-by: Thomas Petazzoni <thomas.petazzoni@free-electrons.com>Signed-off-by: Peter Korsgaard <peter@korsgaard.com> | ||||
| * | openssh: fix sshd for MIPS64 n32 | Vicente Olivert Riera | 2017-06-21 | 2 | -0/+8 |
| ||||||||||||||||||||||||||||||||| | This patch backports two patches that have been sent upstream as a pullrequest in order to fix sshd for MIPS64 n32.The first patch adds support for detecting the MIPS ABI during theconfigure phase.The second patch sets the right value to seccomp_audit_arch taking intoaccount the MIPS64 ABI.Currently seccomp_audit_arch is set to AUDIT_ARCH_MIPS64 orAUDIT_ARCH_MIPSEL64 (depending on the endinness) when openssh is builtfor MIPS64. However, that's only valid for n64 ABI. The right macros forn32 ABI defined in seccomp.h are AUDIT_ARCH_MIPS64N32 andAUDIT_ARCH_MIPSEL64N32, for big and little endian respectively.Because of that an sshd built for MIPS64 n32 rejects connection attemptsand the output of strace reveals that the problem is related to seccompaudit:[pid 194] prctl(PR_SET_SECCOMP, SECCOMP_MODE_FILTER, {len=57,filter=0x555d5da0}) = 0[pid 194] write(7, '000]0005000Ulist_hostkey_types: '..., 97) = ?[pid 193] <... poll resumed> ) = 2 ([{fd=5, revents=POLLIN|POLLHUP},{fd=6, revents=POLLHUP}])[pid 194] +++ killed by SIGSYS +++Pull request: https://github.com/openssh/openssh-portable/pull/71Signed-off-by: Vicente Olivert Riera <Vincent.Riera@imgtec.com>Signed-off-by: Thomas Petazzoni <thomas.petazzoni@free-electrons.com> | ||||
| * | openssh: add support for HW SSL engines | Gilad Ben-Yossef | 2017-05-03 | 1 | -0/+7 |
| |||||||||||| | Enable support for OpenSSH to use a hardware SSL engine ifcryptodev-linux is included. Without this, OpenSSH uses onlyOpenSSL software crypto implementation.Signed-off-by: Gilad Ben-Yossef <gilad@benyossef.com>CC: Baruch Siach <baruch@tkos.co.il>CC: Arnout Vandecappelle <arnout@mind.be>Reviewed-by: Arnout Vandecappelle (Essensium/Mind) <arnout@mind.be>Signed-off-by: Peter Korsgaard <peter@korsgaard.com> | ||||
| * | boot, package: use SPDX short identifier for BSD-2c | Rahul Bedarkar | 2017-04-01 | 1 | -1/+1 |
| ||||||||||| | We want to use SPDX identifier for license string as much as possible.SPDX short identifier for BSD-2c is BSD-2-Clause.This change is done using following command.find . -name '*.mk' | xargs sed -ri '/LICENSE( )?[+:]?=/s/BSD-2c/BSD-2-Clause/g'Signed-off-by: Rahul Bedarkar <rahulbedarkar89@gmail.com>Signed-off-by: Thomas Petazzoni <thomas.petazzoni@free-electrons.com> | ||||
| * | boot, package: use SPDX short identifier for BSD-3c | Rahul Bedarkar | 2017-04-01 | 1 | -1/+1 |
| ||||||||||| | We want to use SPDX identifier for license string as much as possible.SPDX short identifier for BSD-3c is BSD-3-Clause.This change is done using following command.find . -name '*.mk' | xargs sed -ri '/LICENSE( )?[+:]?=/s/BSD-3c/BSD-3-Clause/g'Signed-off-by: Rahul Bedarkar <rahulbedarkar89@gmail.com>Signed-off-by: Thomas Petazzoni <thomas.petazzoni@free-electrons.com> | ||||
| * | openssh: security bump to version 7.5 | Baruch Siach | 2017-03-21 | 2 | -4/+3 |
| ||||||||||||||||||||||||| | From the release notes (https://www.openssh.com/txt/release-7.5):Security-------- * ssh(1), sshd(8): Fix weakness in CBC padding oracle countermeasures that allowed a variant of the attack fixed in OpenSSH 7.3 to proceed. Note that the OpenSSH client disables CBC ciphers by default, sshd offers them as lowest-preference options and will remove them by default entriely in the next release. Reported by Jean Paul Degabriele, Kenny Paterson, Martin Albrecht and Torben Hansen of Royal Holloway, University of London. * sftp-client(1): [portable OpenSSH only] On Cygwin, a client making a recursive file transfer could be maniuplated by a hostile server to perform a path-traversal attack. creating or modifying files outside of the intended target directory. Reported by Jann Horn of Google Project Zero.[Peter: mention security fixes]Signed-off-by: Baruch Siach <baruch@tkos.co.il>Signed-off-by: Peter Korsgaard <peter@korsgaard.com> | ||||
| * | openssh: Move key generation to the start function of init script. | Ignacy Gawędzki | 2017-02-26 | 1 | -3/+3 |
| |||||||||| | Since there's not much point in generating missing host keys when theinit script is called with 'stop', the call to ssh-keygen should notbe done inconditionally, but in the start function instead.Signed-off-by: Ignacy Gawędzki <ignacy.gawedzki@green-communications.fr>Acked-by: 'Yann E. MORIN' <yann.morin.1998@free.fr>Signed-off-by: Thomas Petazzoni <thomas.petazzoni@free-electrons.com> | ||||
| * | packages: improve license type lists | Danomi Manchego | 2017-02-20 | 1 | -1/+1 |
| ||||||||||||||| | Make license type lists more uniform:* put content license applies to in parenthesis; ex: 'GPLv2+ (programs)'* use commas to separate types listed without conjuction; ex: 'GPLv2, LGPLv2'No attempt was made to validate the claimed licenses. This is just a tweakto increase uniformity of the _LICENSE variables.Signed-off-by: Danomi Manchego <danomimanchego123@gmail.com>Reviewed-by: Thomas Petazzoni <thomas.petazzoni@free-electrons.com>[Thomas: replace semi-colons by commas in LIBURCU_LICENSE.]Signed-off-by: Thomas Petazzoni <thomas.petazzoni@free-electrons.com> | ||||
| * | openssh: security bump to version 7.4p1 | Gustavo Zacarias | 2016-12-19 | 3 | -34/+3 |
| ||||||||||||||||||||| | Fixes:CVE-2016-10009 - ssh-agent(1): Will now refuse to load PKCS#11 modulesfrom paths outside a trusted whitelistCVE-2016-10010 - sshd(8): When privilege separation is disabled,forwarded Unix-domain sockets would be created by sshd(8) with theprivileges of 'root'CVE-2016-10011 - sshd(8): Avoid theoretical leak of host private keymaterial to privilege-separated child processes via realloc()CVE-2016-10012 - sshd(8): The shared memory manager used bypre-authentication compression support had a bounds checks that could beelided by some optimising compilershttp://seclists.org/oss-sec/2016/q4/708Drop upstream patch.Signed-off-by: Gustavo Zacarias <gustavo@zacarias.com.ar>Signed-off-by: Peter Korsgaard <peter@korsgaard.com> | ||||
| * | openssh: add upstream security fix | Baruch Siach | 2016-11-15 | 1 | -0/+31 |
| ||||||| | Fixes CVE-2016-8858: Memory exhaustion, up to 128MB, of unauthenticated peer.Signed-off-by: Baruch Siach <baruch@tkos.co.il>Signed-off-by: Thomas Petazzoni <thomas.petazzoni@free-electrons.com> | ||||
| * | openssh: bump version to 7.3p1 | Vicente Olivert Riera | 2016-08-01 | 2 | -3/+3 |
| ||||| | Signed-off-by: Vicente Olivert Riera <Vincent.Riera@imgtec.com>Signed-off-by: Thomas Petazzoni <thomas.petazzoni@free-electrons.com> | ||||
| * | toolchain: add hidden symbol for PIE support | Waldemar Brodkorb | 2016-07-24 | 1 | -6/+1 |
| ||||||||||||| | uClibc-ng does not support PIE for some architectures asarc and m68k. It isn't implemented in the static linking case, too.With musl toolchains you might have static PIE support with littlepatching of gcc. Static linking for GNU libc isn't enabled inbuildroot. Fixup any package using special treatment of PIE.(grep -ir pie package/*/*.mk)Signed-off-by: Waldemar Brodkorb <wbx@openadk.org>[Thomas: use positive logic.]Signed-off-by: Thomas Petazzoni <thomas.petazzoni@free-electrons.com> | ||||
| * | openssh: security bump to version 7.2p2 | Gustavo Zacarias | 2016-03-10 | 2 | -2/+2 |
| ||||||||| | Fixes:CVE-2016-3115 - sanitise X11 authentication credentials to avoid xauthcommand injection when X11Forwarding is enabled.Signed-off-by: Gustavo Zacarias <gustavo@zacarias.com.ar>Signed-off-by: Peter Korsgaard <peter@korsgaard.com> | ||||
| * | openssh: bump to version 7.2p1 | Gustavo Zacarias | 2016-02-29 | 2 | -3/+3 |
| ||||| | Signed-off-by: Gustavo Zacarias <gustavo@zacarias.com.ar>Signed-off-by: Thomas Petazzoni <thomas.petazzoni@free-electrons.com> | ||||
| * | openssh: security bump to version 7.1p2 | Gustavo Zacarias | 2016-01-14 | 2 | -4/+3 |
| |||||||||||||||||| | Fixes:CVE-2016-0777 - Client Information leak from use of roaming connectionfeature.CVE-2016-0778 - A buffer overflow flaw was found in the way the OpenSSHclient roaming feature was implemented. A malicious server couldpotentially use this flaw to execute arbitrary code on a successfullyauthenticated OpenSSH client if that client used certain non-defaultconfiguration options.Signed-off-by: Gustavo Zacarias <gustavo@zacarias.com.ar>Reviewed-by: James Knight <james.knight@rockwellcollins.com>Tested-by: James Knight <james.knight@rockwellcollins.com>Signed-off-by: Peter Korsgaard <peter@korsgaard.com> | ||||
| * | package: Replace 'echo -n' by 'printf' | Maxime Hadjinlian | 2015-10-04 | 1 | -2/+2 |
| |||||||||||| | 'echo -n' is not a POSIX construct (no flag support), we shoud use'printf', especially in init script.This patch was generated by the following command line:git grep -l 'echo -n' -- `git ls-files | grep -v 'patch'` | xargs sed -i 's/echo -n/printf/'Signed-off-by: Maxime Hadjinlian <maxime.hadjinlian@gmail.com>Reviewed-by: Arnout Vandecappelle (Essensium/Mind) <arnout@mind.be>Signed-off-by: Peter Korsgaard <peter@korsgaard.com> | ||||
| * | openssh: fix static compilation | Waldemar Brodkorb | 2015-08-29 | 1 | -0/+4 |
| |||||||||| | PIE and static doesn't work on Linux.Fixes:http://autobuild.buildroot.net/results/dce/dce0202e039f4636d68532c4aab8738938b76650/Signed-off-by: Waldemar Brodkorb <wbx@openadk.org>Signed-off-by: Thomas Petazzoni <thomas.petazzoni@free-electrons.com> | ||||
| * | openssh: security bump to version 7.1p1 | Gustavo Zacarias | 2015-08-25 | 2 | -3/+4 |
| ||||||||||||| | Fixes:CVE-2015-6563 - Fixed a privilege separation weakness related to PAMsupport.CVE-2015-6564 - Fixed a use-after-free bug related to PAM support thatwas reachable by attackers who could compromise the pre-authenticationprocess for remote code exectuion.CVE-2015-6565 - incorrectly set TTYs to be world-writable.Signed-off-by: Gustavo Zacarias <gustavo@zacarias.com.ar>Signed-off-by: Peter Korsgaard <peter@korsgaard.com> | ||||
| * | openssh: selinux and pam support | Matt Weber | 2015-07-18 | 1 | -0/+16 |
| ||||||||| | [Thomas: in the sed expression, use % as a delimiter instead of /,since the line contains several / that all had to be escaped.]Signed-off-by: Matthew Weber <matthew.weber@rockwellcollins.com>Reviewed-by: Samuel Martin <s.martin49@gmail.com>Signed-off-by: Thomas Petazzoni <thomas.petazzoni@free-electrons.com> | ||||
| * | openssh: bump to version 6.9p1 | Gustavo Zacarias | 2015-07-02 | 2 | -3/+3 |
| ||||| | Signed-off-by: Gustavo Zacarias <gustavo@zacarias.com.ar>Signed-off-by: Thomas Petazzoni <thomas.petazzoni@free-electrons.com> | ||||
| * | package: kill pointless text justification | Gustavo Zacarias | 2015-04-23 | 1 | -1/+1 |
| |||||| | Signed-off-by: Gustavo Zacarias <gustavo@zacarias.com.ar>Acked-by: Arnout Vandecappelle (Essensium/Mind) <arnout@mind.be>Signed-off-by: Thomas Petazzoni <thomas.petazzoni@free-electrons.com> | ||||
| * | openssh: move systemd service files to /usr/lib | Mike Williams | 2015-03-20 | 1 | -2/+2 |
| ||||| | Signed-off-by: Mike Williams <mike@mikebwilliams.com>Signed-off-by: Thomas Petazzoni <thomas.petazzoni@free-electrons.com> | ||||
| * | openssh: bump to version 6.8p1 | Gustavo Zacarias | 2015-03-18 | 3 | -42/+24 |
| ||||| | Signed-off-by: Gustavo Zacarias <gustavo@zacarias.com.ar>Signed-off-by: Thomas Petazzoni <thomas.petazzoni@free-electrons.com> | ||||
| * | package/*: rename patches according to the new policy | Peter Korsgaard | 2015-02-03 | 2 | -0/+0 |
| ||||||| | Autogenerated from rename-patch.py (http://patchwork.ozlabs.org/patch/403345)Signed-off-by: Samuel Martin <s.martin49@gmail.com>Signed-off-by: Peter Korsgaard <peter@korsgaard.com> | ||||
| * | package: indentation cleanup | Jerzy Grzegorek | 2014-12-24 | 1 | -2/+8 |
| ||||| | Signed-off-by: Jerzy Grzegorek <jerzy.grzegorek@trzebnica.net>Signed-off-by: Thomas Petazzoni <thomas.petazzoni@free-electrons.com> | ||||
| * | package/*/*.mk: Fix indent | Maxime Hadjinlian | 2014-11-08 | 1 | -1/+1 |
| |||||||| | Fix indent for LIBFOO_USERS and LIBFOO_PERMISSIONS as per the manual example.Signed-off-by: Maxime Hadjinlian <maxime.hadjinlian@gmail.com>Acked-by: Arnout Vandecappelle (Essensium/Mind) <arnout@mind.be>Signed-off-by: Peter Korsgaard <peter@korsgaard.com> | ||||
